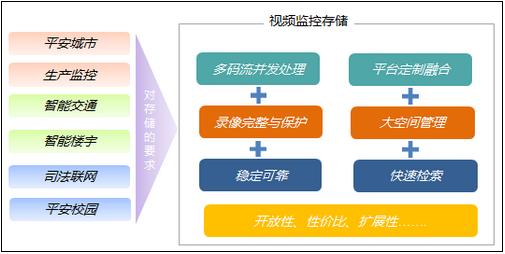
In recent years, with the continuous development of information technology and the popularization and application of security products and systems, the data security issues in the security industry have been receiving more and more attention. With the rapid development of high-definition surveillance, large-scale projects such as safe cities and smart cities have been widely deployed, and the amount of data has been increasing. The storage problems and data security problems under big data have gradually become video network monitoring. New topics in the field.
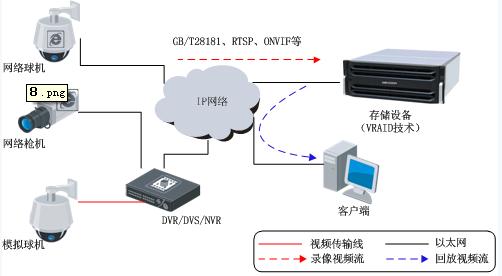
The storage of the embedded data is accompanied by the development of security technology and storage technology. It has experienced the stages of analog front end + DVR storage, analog front end + DVS / DVR + network storage, network front end + NVR, network front end + network storage. Now with the increase of network bandwidth, HD applications are becoming more and more popular, and higher requirements are put forward for security storage systems.
First, security data storage new requirements
The characteristics of today's security development can be summarized as the following three points:
1) HD
â— High-line simulation: 600/650/700 line analog camera + high-resolution DVR
â— Digital HD: SDI/HDSDI, HDCCTV
â— HD network: 1.3 million / 2 million / 5 million IPC + HDVR + NVR, 4K applications
2) Intelligent
â— Engage in post-responsibility, passive application to prevent and control, proactive defense, further liberate manpower and improve efficiency
â— From the technical level of intelligent analysis to the actual application phase, such as perimeter prevention, personnel tracking, etc., has been used in the public security, transportation, finance, justice and other industries
3) Fusion application
From the single system independent use to the multi-system platform integration use phase, the main performance is
â— Large-capacity video information collection and sharing
â— Internal integration of security system, docking upper management system
â— Multi-system integration, such as emergency linkage, emergency deployment control, public security fire protection, etc.
â— Security and IT technology are highly integrated
According to the new requirements of the current security system, the requirements for the security storage system can be summarized as follows.
Second, security storage technology: protect data security from the bottom
From the above analysis, the security system has entered the actual stage, and the actual operations of intelligent analysis, active defense, and fusion applications must be built on a reliable monitoring data storage system. Here are two RAID technologies that ensure secure storage of data from the bottom layer.
1, VRAID (VedioRAID) technology
RAID technology is very familiar. It belongs to the basic technology of disk array. After continuous development, there are now eight basic RAID levels from RAID 0 to RAID7 and two-dimensional RAID like RAID 10 and RAID 50. Different RAID levels can be Users provide the appropriate RAID performance and data security. However, any RAID technology has a fault tolerance limit. After the number of bad disks reaches a certain number, the entire RAID group fails, and all the data is lost. For example, in the traditional RAID5, when a hard disk is damaged, RAID can ensure that the data is not lost through the redundancy mechanism, but when the hard disk is damaged more than 2 pieces, it is unfortunate that RAID5 can not help you recover the hard disk data. Generally, you have to share all the data with you. Say bye bye!
The VRAID technology introduced here is a new RAID technology for security applications (Hikvision's new technology for video applications). VRAID technology can effectively solve the problem of complete loss of data in the entire RAID group after multiple (2 or more) hard disks in traditional RAID are damaged. That is, VRAID has more than 2 bad disks (ideally, as long as there is one available disk), the data in the remaining good disks is still readable, and the new data can be continuously written.
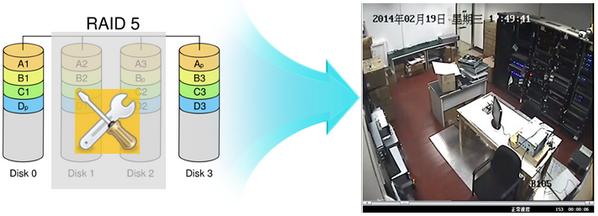
Technical principle: The implementation of VRAID is based on the streaming data management structure and RAID optimization technology of the storage device under the traditional file system. When multiple disks in VRAID are damaged, under the streaming media data management structure, the video data in each strip on the good disk can still be played independently; when playing to the bad disk strip, it will automatically skip and automatically play the next available. The data on the strip ensures that the video is played smoothly. At the same time, when new data is transmitted, it can still be written.
2, network RAID technology
Traditional RAID is limited by the number of hard disks. In the era of rapid data capacity, it cannot meet the needs of enterprises for unified and flexible deployment of resources. The intelligent and efficient development trend of storage requires that the underlying data distribution architecture must be highly flexible and scalable. As the capacity of hard disks increases, it is increasingly difficult to manage data on a hard disk. A general disk array can only be RAID inside the same physical node, and a hard disk can only be located in one RAID group. When the controller is down or the disk is damaged, all the data is lost. This is the traditional Disk array RAID availability is a major disadvantage.
Network RAID is a Scale out technology that enables RAID to be established between different physical nodes through network communication. And the basic unit that makes up the RAID is no longer the entire hard disk, but each hard disk Chunk block, one hard disk can be in multiple RAID groups. When a physical node is down, the data of the entire system can be recovered through other physical nodes; when a single hard disk fails, multiple disks can participate in the reconstruction together, and the reconstruction process can be completed in minutes.
Technical principle:
1) Divide all hard disks of each physical node into Chunk blocks
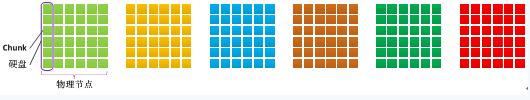
2) Create RAID based on hard disk Chunk blocks of different physical nodes
The entire RAID is built based on the Chunk, which comes from a disk of a different physical node. The entire RAID group can be built by all physical nodes (one or more hard disks).
The first set of RAID: 3+1--3 valid data, 1 check data
The second group of RAID: 3 + 2 - 3 valid data, 2 check data
3) Single hard disk failure and processing
A hard disk can be located in multiple sets of RAID. Therefore, when a single hard disk is damaged, multiple sets of RAID will be reconstructed together. In the extreme case, all hard disks participate in the reconstruction calculation at the same time, and the speed is greatly improved compared with the normal RAID. Even seconds.
4) The entire physical node failure and processing
Assume that the third device is faulty. In normal RAID, data of the entire device is lost.
In network RAID, the impact on each RAID is as shown below. Only some of the Chunk data in each RAID group is lost, and the remaining data blocks in the RAID can be completely recovered.

  3+1RAID 3+2RAID
Although network RAID is called RAID, it is actually a distributed storage technology. It can solve the problem of long reconstruction time under common RAID, large management burden when multiple storage nodes are stacked, unable to meet hotspot requirements, data loss during node failure, and eliminate greater system availability risk.
In network RAID, the entire disk is no longer used as the management unit and the verification unit. The disk segment management (Chunk) is managed to zero, providing fine management, high-level fault tolerance and high-performance data recovery, providing high data storage. reliability.
In network RAID, the general disk error can be reconstructed in the second level; when the disk fails, a large number of disks participate in the reconstruction, and the reconstruction process is accelerated ten times; the storage resource is allocated across nodes, the management is simpler, and more importantly, the whole When a node fails, data is guaranteed to be lost. The highly fault-tolerant design, whether it is a bad disk or node replacement and expansion, can be easily handled and implemented to improve the continuous availability of the overall storage solution.
Third, security data storage future
The development of security storage must be the coordinated development of the underlying technology, physical equipment, and system architecture. It is impossible to meet the demand by relying on any single point.
For the usual large, medium and small monitoring systems, the video streaming write-through storage architecture without storage server + security-oriented VRAID technology can simplify system deployment and fully protect users' data security. At the same time, with the implementation of the GB/T28181 standard, the video streaming direct write storage solution using the standard streaming media protocol will be more and more favored by the market.
For very large-scale monitoring systems (tens of thousands of video front-ends), it is required to achieve PB-level storage capacity. Single-device stacking and common file systems cannot provide secure and efficient application guarantees. Virtualization, clustering, and discrete storage are required. s solution. The video cloud storage technology for security applications adopts the cloud computing concept, and the underlying network RAID technology can provide users with virtualized, clustered and integrated convenient cloud storage services.
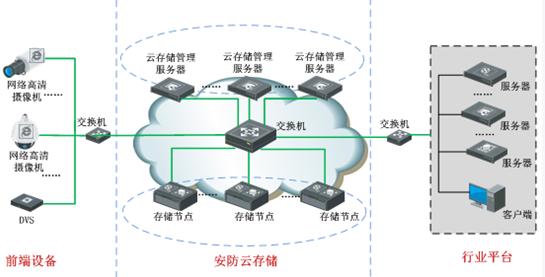
Security cloud storage system features:
1) Virtualization technology fully integrates storage capacity, allocates on demand and can be flexibly sized.
2) The front end writes cloud storage directly through the video streaming protocol, saving user investment.
3) The video stream equalizes the slice through a discrete algorithm to provide data concurrent services in a cluster response manner.
4) The bottom layer uses network RAID technology to protect user data at multiple levels.
5) The whole system cluster working mode ensures real-time load balancing of services between devices and improves device utilization.
6) Global integrated indexing technology, comprehensively improve the query rate and achieve a second-level response.
Security cloud storage solves the problem that the current security industry has begun to face the management and application of massive data storage. From 2012 to 2013, Hikvision has successfully applied several safe city projects, and has achieved great success through user actual use. Video business application experience. In the next few years, in the construction of large and medium-sized security projects, security cloud storage will occupy the main position of video surveillance storage solutions. It is believed that security cloud storage will soon develop into a mainstream solution for the video surveillance storage market, and it will be the best choice. Program.
Grinding Glass Beads, Resistance thermolastic Glass Beads for Grinding Glass Beads for Grinding,Road Marking,Blasting, Glass Beads ,with the advantages of smooth surface, even size, high hardness, wearable and stable, widely used as disperser, grinding media and filler materials in day, paint, ink and chemical industry etc.
Grinding and Polishing Glass Beads :
Size:0.8-1mm;1.0-1.5mm;1.5-2mm;2.0-2.5mm; 2-3mm;2.5-3mm; 3-4mm; 4-5mm; 5-6mm etc.
The ability to operate a mill with smaller-diameter grinding media greatly increases the mill's efficiency and can overall further increase the quality of product through finer grinding. However, smaller Glass beads are more prone to hydraulic packing due to their decrease in mass per bead. Hydraulic packing occurs when the drag flow from the product pulls the media with the product and ultimately causes media packing around the discharge screen.
Glass beads have replaced the conventional grinding media : Ottawa sand, Steel balls, Pebbles, Ceramic balls etc. in Sand mills, Ball mills, Attrition mills for the following simple reasons :
They do not react or get reacted with the materials that are ground.
Being spheres, every bead in charge takes important part in the grinding operation.
They have smooth glassy surfaces and hence slide without much friction there by reducing the load on the stirring mechanism.
Glass beads are of interest to the following industries:
a) Paints. b) Pigments. c) Ink & Printing Inks. d) Dyes. e) Chemicals. f) Cosmetics.
g) Gums & Waxes.
Grinding Glass Beads
Polishing Blasting Grinding Glass Beads , Milling and Grinding Glass Beads Grits, Abrasive Jetting Grinding Glass Beads, Grinding Media Spheres Grinding Glass Beads
YONGQING BAILUYUAN GLASS PRODUCTS CO.,LTD , http://www.blyglassbeads.com